Secure and Control Public Network Access Availibility
WiFi access in public places like stadiums, trains, airports, shopping centres and parks has become commonplace in our society. Sadly though, these infrastructures often lack the security and management tools necessary to provide a good quality of experience. A public network is exposed to many types of threats, intentional and unintentional, that have impact on the service.
Slow DDoS, or Slow Distributed Denial-of-Service, is one of those threats that WiFi networks are exposed to—a growing problem that needs addressing for security reasons. Using only conventional technology against DDoS doesn’t suffice against Slow DDoS: Slow DDoS is designed to remain virtually invisible in DDoS detector software. Security Analytics working together with the firewall in a closed loop operation is needed.

SOLUTION
Protect WiFi Network Operations with Slow DDoS
Detection and Mitigation
People seek connectivity with WiFi networks with all sorts of devices, and there is no way of knowing what firmware update they have. The behavior of these devices can be very different and while individually they may not be harmful, collectively they can cause problems. Imagine for instance a user with a wrongly configured password in combination with a device that has aggressive retry procedures and hammers the authentication server with requests. If hundreds of such users connect to the network at the same time, their combined access requests load to the authentication server may cause problems.
Each of the devices may have back-off algorithms build in, but as they retry over time persistently, collectively the load on the servers will anyway become unbearable causing service disruption for other users.
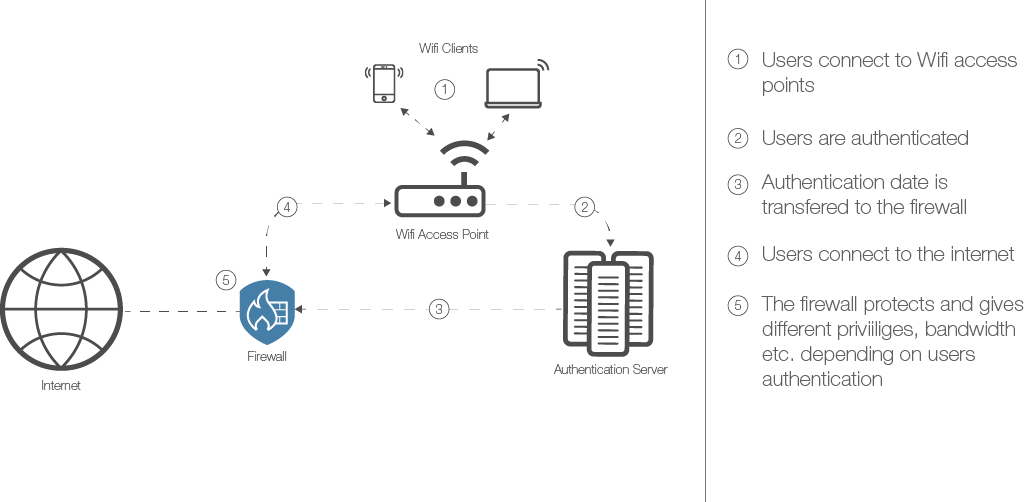
The solution requires the firewall to have intimate knowledge of what transitions belong to what user. RADIUS spoofing is used to map sessions to user-ids, and in this way also unauthenticated session can be identified. The security analytics engine connected to the firewall can spot repetitive unauthenticated sessions from unique device IDs and initiate action to implement mitigation strategies. Misbehaving devices can put in quarantine zones until the algorithm determines that they ready to forward a live access attempt again.
These type of automated operations to secure the continuity of the network services is critical in public networks where anything and anyone can connect and have an impact on the experience for others.
BENEFITS
1
Enable low latency endpoints
2
Direct devices communication
3
Built for scalability
Use Cases included in this solution
Firewalling
Intrusion detection and prevention system, GeoIP restrictions and denial of service protection
READ MOREProducts

Desktop Models
Compact, fast and extremely powerful, these appliances deliver security performance for remote offices or as CPEs.

Rack-mounted Models
For the larger enterprise users, these appliances give best in class protection for even the biggest companies.

Virtual Models
Clavister has been a pioneer in virtual products since 2008. Find out how virtual NGFWs might be the answer for your needs.

Security Subscriptions
Clavister’s services and knowledge products help you realize the full potential of your newly secured network.





