All Military Platforms Need Embedded Cyber Defence
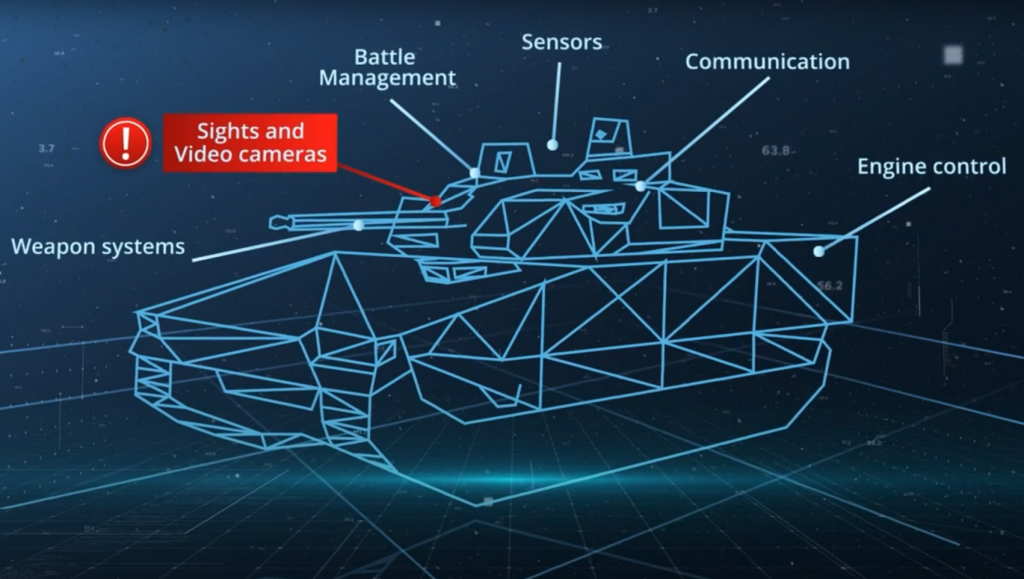
Traditional armour is no longer enough since technology advancements and increased connectivity have reached the point where military platforms and weapon systems could be taken out by cyber attacks.
Defence manufacturing depends on complex supply chains. In many cases, a single armoured vehicle is made up of components from hundreds of different suppliers. And while there is an increased awareness for cyber security in general, not all sub-suppliers may have the same level of security in their product processes, which makes them vulnerable for supply chain attacks, especially for cyber infiltration and sabotage.
Clavister Solution
Cyber Armour – Securing All Communication Channels
Clavister Cyber Armour is a power-packed Next-Generation Firewall (NGFW) for in-vehicle deployment. It includes a cyber security gateway that connects all digital sub-systems (depending on the requirements) and controls the internal communication flow to prevent and limit the impact of cyberattacks. For enhanced detection and response, a bespoke Artificial Intelligence (AI) engine continuously monitors the communication traffic, detects the cyber attacks in real time and self-learns to mitigate against new and unknown cyber threats.
DOWNLOAD BROCHUREEnhance Military Platform Survivability
Cyber Armour can be embedded from the design phase of a military platform or introduced as part of upgrades and modernisation programs as the hardware can be tailored and optimised for each military platform. It allows military vehicles to continue to operate even after cyber breach attempts, thereby, increasing military vehicles’ survivability covering its entire lifespan.
FUTURE READY
Powerful and extremely efficient Artificial Intelligence (AI) engine that enables system to self-learn and protect against the cyberattacks of tomorrow.
FLEXIBLE DEPLOYMENT
Virtualised or hardware based as per customer requirements. Integrated directly into the military platform/vehicle.
MADE IN EUROPE
Coming from a European vendor, Cyber Armour is free from ITAR restrictions (USA defence technology export restrictions)
Cyber Armour – Key Features
Cyber Armour protects military platforms, such as armoured vehicles, against cyber attacks and exposed vulnerability through wireless connectivity, maintenance, tampering and more. Cyber Armour can work with all kinds of military platforms, across land, sea, air and space.
ADVANCED NETWORK SECURITY
Cyber Armour is a NGFW that provides full features of a Unified Threat Management (UTM) solution enabling large set of use cases for military plaforms. It secures the communication data and provides active protection against advanced cyber threats.
SELF-LEARNING ARTIFICIAL INTELLIGENCE (AI)
Cyber Armour is powered with advanced Artificial Intelligence (AI) engine, that not only provides active protection but also detects and responds to cyber attacks, providing a complete cyber security solution for defence platforms and military vehicles.
View AI InfographicMILITARY GRADE HARDWARE
Through a proven process, Cyber Armour’s hardware can be customised and ruggedised according to customer specifications and required military standards.
CENTRALISED THREAT ANALYTICS
Logs and events are generated continuously and can be transferred, live via over a network or manually for post processing.
NETWORK SEGMENTATION
Network segmentation physically separates different communication networks like CAN bus and ethernet, allowing you to have complete visibility and control over data traveling between different networks.
POWERFUL SOFTWARE PLATFORM
Our unique operating system, cOS Core, has been built from the ground-up, providing transparency and compliance for defence procurement. Own operating system means we have complete R&D control of Cyber Armour.
Whitepaper: Defend the Defenders
Are you looking for cyber hardening of your military equipment or end-to-end cyber security for your platform?
Read more in our whitepaper or contact us today to discuss your requirements!
Client Testimonial
Don’t take our word for it – here’s what our clients say:
“The digitalisation has accelerated in the last 10 years. A modern combat vehicle is a node in a network and a sensor station. With all this increased connectivity, cyber security needs to be at the forefront. This is what we have been doing with Clavister and we are proud to say that CV90 is one the most secure IFVs on the market today”.
BAE SYSTEMS

Clavister Expert for Defence
Stefan has over 20 years of experience in the technology market and he serves as part-time officer (Major) in Swedish Army. Stefan is passionate about defence cyber and his current focus is working with partners and building consortiums to develop European cyber capabilities.
Stefan Brodin, Head of Defence Solutions
CONTACT STEFANSolutions for Defence
Different defence industry use cases that Clavister provides cyber security solutions for:
Military Grade Network Security
Next-Generation Firewalls – ruggedised, non-ruggedised and virtual. Developed in Europe and Common Criteria Certified (EAL4 ).
Cyber Security Expertise
Clavister’s Cyber Security as-a-Service to gain access to key competencies to develop and maintain sufficient cyber protection.
AI-Powered Jamming Detection
Utilise AI and advanced algorithms for jamming detection to secure satellite-ground station communication links.