Protecting the Cloud and Datacenter Infrastructure from external threats
In a cloud environment you have no idea who your neighbour is. Yet the virtual resources are seldom protected from each-other by the cloud supplier. For those system integrators that are aiming to become Managed Security Service Providers, Clavister provides the perfect lean solution that can provide isolation of customer’s resources on shared infrastructure.


SOLUTION
Micro Segmentation
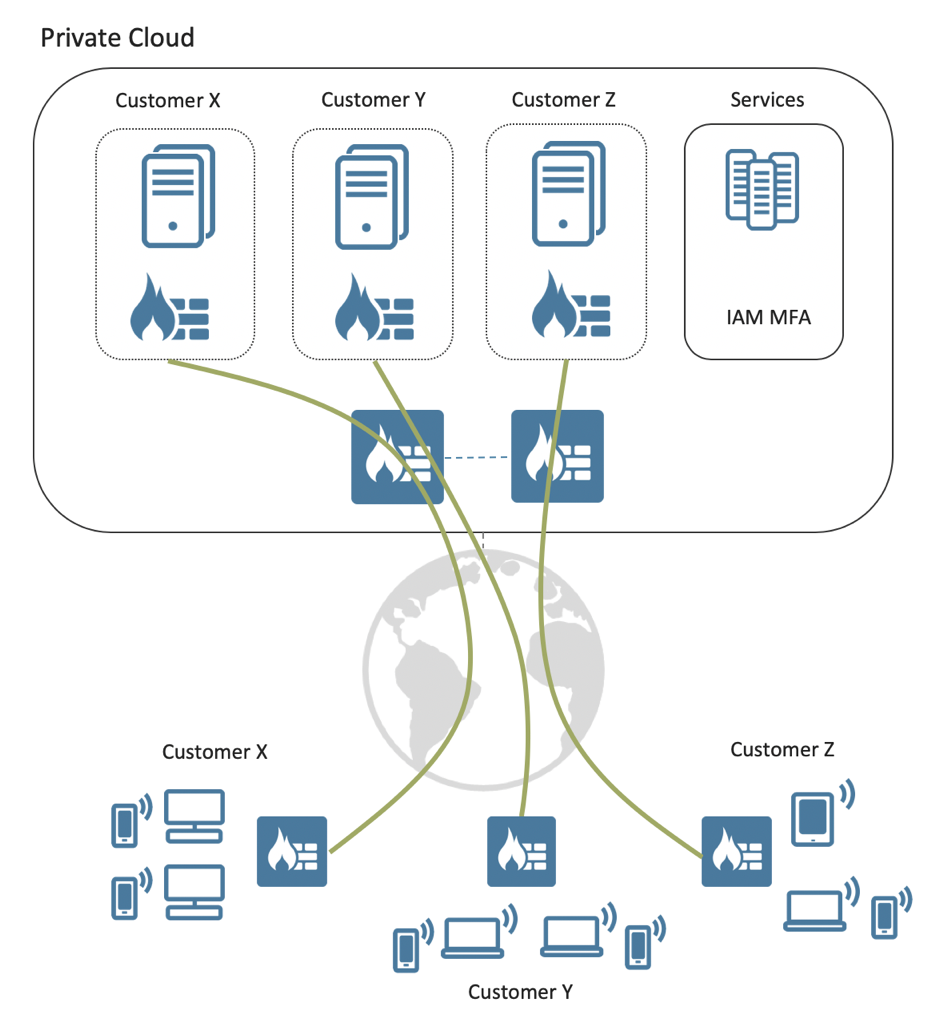
With a small firewall image hosted virtualised in a cloud infrastructure, the solution allows all the traffic to be routed through that node, providing full control and protection capabilities. Strict traffic policies can be implemented segmenting the traffic in a controlled manner. Also, intrusion detection and antivirus can be enabled to securely scan all the traffic going into the private cloud environment.
The result is isolated private cells where traffic can be controlled individually writing the customers’ virtual environment and towards the office VPN and outside world. An ideal addition to this use-case is remote workers configured with always on VPN proxying their traffic through the corporate firewall.
BENEFITS
1
Isolated Secure Cells for each customer’s virtual images
2
Cost efficient to supply full NGFW capabilities
3
End-to-end tunnelled security, from the customers’ site to their virtual images
Use Cases
The following use cases are included in this solution:
Reliable Secure VPN
Connecting branch offices and remote locations securely and cost effectively
READ MOREProducts

Desktop Models
Compact, fast and extremely powerful, these appliances deliver security performance for remote offices or as CPEs.

Rack-mounted Models
For the larger enterprise users, these appliances give best in class protection for even the biggest companies.

Virtual Models
Clavister has been a pioneer in virtual products since 2008. Find out how virtual NGFWs might be the answer for your needs.

Security Subscriptions
Clavister’s services and knowledge products help you realize the full potential of your newly secured network.





