Protecting your business from dangerous content
Over 90% of the web traffic is encrypted today already and an estimated 50% of attacks high inside secure traffic. It is a good strategy to equip all your endpoint with anti-virus scanning software – as attacks can be identified at the client as the traffic gets decrypted.
But there are problems with this approach – scanning is not available on all type of clients, its resource consuming slowing down employee’s equipment and it most often required frequent signature update to stay up to date.


SOLUTION
Advanced Threat Detection
With an Advanced Threat Detection product run complementary to the firewall, dedicated resources are focused on scanning content holistically and efficiently – with multiple scanning engines. Predictive engines based on AI and Machine Learning are capable of even stopping the Zero-Day attacks due to their behaviour analysis approach.
If there still is a high uncertainty of what the executable will do – then Sandbox comes in. An environment outside the perimeter enables controlled detonation of the executable – identifying exactly what it does – without allowing it to make any impact.
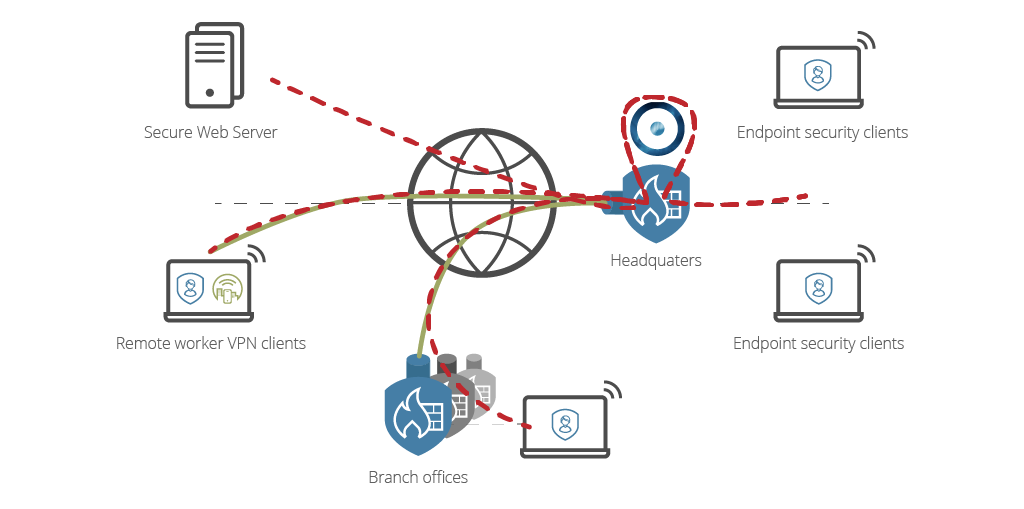
This setup not only secures all traffic proxied through the main HQ firewall, it also scans traffic coming in from branch offices and remote workers via VPN. In an ideal setup the VPN client on the remote computer are setup to always connect and proxy all traffic. This allows the Advanced Threat Inspection product to protect the whole office – on-site, at remote sites and even the workers on the road.
BENEFITS
1
Thorough inspection even of encrypted traffic with multiple scanning engines
2
Remote workers securely protected the same as in the office thanks to always-on VPN
3
Efficient threat inspection for the whole enterprise with offloaded firewall infrastructure
Use Cases included in this solution
Featured products for this solution

Clavister NetEye Cloud
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Clavister NetEye
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.

Clavister OneConnect
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.