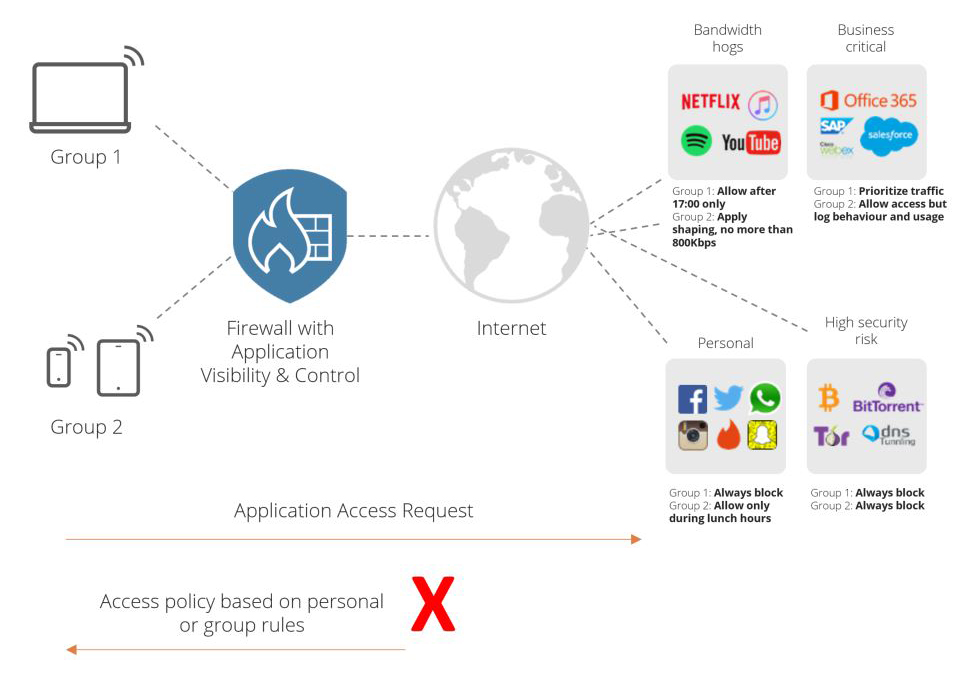
THE PROBLEM
Enterprise IT administrators need to control the usage of their network to ensure it’s used for business applications. Some of these applications may even deserve priority while others should be pro-actively blocked—as they
are known to carry higher risks and compromise security. An example is BitTorrent clients for peer-to-peer file downloading or Tor, an application to browse the dark-web and commonly used by malware to exfiltrate data from your network.
Another example is unauthorized excessive usage of server resources for BitCoin mining, spiking up a company’s electricity bill. These
applications should be blocked.
Not all traffic is web traffic—a lot of traffic runs on separate ports and uses custom protocols to communicate with it’s servers and peers.
Therefore an Application Identification (also called deep packet inspection/DPI) engine is required to detect the application or service accurately. An application like WebEx and Skype can be identified and it’s traffic can be prioritized to aid in the quality of the conversations. Application control is essential to improve the user’s experience.
SOLVING THE PROBLEM
To manage in a controlled way the traffic from your users, Clavister’s Next Generation Firewall includes the world’s best deep packet inspection technology to do application identification. In addition, Clavister has classified each application with a risk level from very low to very high, making configuration of blocking risky applications a breeze.
VIRTUAL & APPLIANCE
Unique Risk Level determined for each application
MANAGE BANDWIDTH
Identification to block/allow access and manage bandwidth
DPI TECHNOLOGY
Integrated application identification through Deep Packet Inspection (DPI) technology
BEST OF BREED BY ENEA / QOSMOS
Clavister integrates Qosmos’ ixEngine by ENEA who leads the market for IP traffic classification and network intelligence technology. Just like finding a birch tree in a pine forest based on the trees characteristics, Qosmos identifies 3000+ unique applications out of network traffic. The definitions are updated continuously with every release of our software scheduled on a monthly basis. For more information visit www.qosmos.com

Internet of Things (IoT)
Specifically for IoT devices, application visibility provides the perfect means to control what the devices are doing. With advanced policies you can restrict them only to be allowed to do what they are support to do on the network. So that even if an IoT device is hacked it cannot be used as a springboard to reach other resources.
THE RESULT
Application control provides the means to be very specific on what you want to allow on your network. This increases the security levels and enables you to use new technologies early without taking unnecessary risks.
1
REDUCE RISK LEVEL
Reduce risk level by blocking access to class 4 & 5 identified apps
2
EMPLOYEE PRODUCTIVITY
Increase employee productivity by time restricting or blocking distracting apps
3
PRIORITIZE CRITICAL APPLICATIONS
Prioritize critical applications & control bandwidth usage by streaming apps
Solutions & Customers
The following solutions and customers benefit from this use-case:
SOLUTION
Secure SD-WAN
Optimise business connectivity and security across multi-site locations
SOLUTION
OT Micro Segmentation
Segementation on the factory floor with application based policy
CASE STUDY
Regus
Workplace-as-a-Service company
connecting 3 000 centers in 100 countries