THE PROBLEM
More and more of our web transactions use encryption. According to Google 80% of pages loaded in Chrome on Windows are HTTPS, up from 69% last year. But encryption does not mean content is safe. There’s a high risk that threats enter the perimeter via secure transactions. Major analysts predict that > 50% of all network attacks hide in SSL traffic.
This allows hackers to embed malicious code in a secure web session and get malware onto client’s desktops. What’s needed is reliable decryption and inspection of the incoming traffic from untrusted sources.
However, impact to the Firewall infrastructure must be minimal to reduce operational cost—and testing house NSS Labs has reported that enabling SSL Inspection has a 60%–80% drop in the average throughput on NGFWs with the functionality built in (!).

SOLVING THE PROBLEM
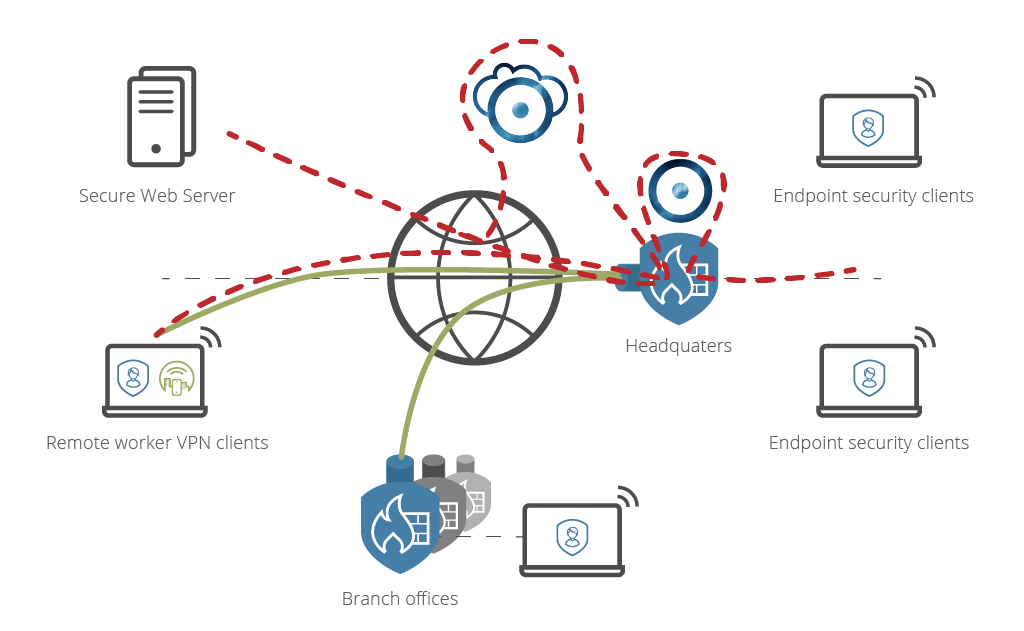
Instead of tripling or quadrupling the security perimeter infrastructure you can complement the firewall with Advanced Threat Protection. HTTP & HTTPS Request are routed to the external Advanced Threat Protection appliance or cloud service where the traffic is decrypted, the content scanned, and harmful downloads removed.
In the firewall you simply configure selective routing for relevant traffic that needs to be inspected. The Advanced Threat Protection adjunct performs full SSL decryption and utilizes multiple scanning engines to validate the traffic. When in doubt, executable files are forwarded to a Sandbox in the cloud to perform a controlled detonation outside the perimeter. No further firewall investment at the perimeter is required. With a solution deployed in the Cloud the traffic is transported securely in an IPsec tunnel and will scale with your needs.
THE RESULT
Advanced Threat Protection will give the business owner peace of mind knowing that all content downloaded is scanned for threats. Risky files are taken to a sandbox for secure detonation outside the enterprise perimeter. The solution has limited to no impact on firewall performance and can be easily scalability with a cloud deployment.
1
Deep traffic inspection
2
No impact on firewall performance
3