What Zero Trust Network Access (ZTNA) is and why businesses need it

The need for robust cyber security has never been higher than it is today. Almost every day news outlets write about companies being hacked, victims of ransomware or similar. The old way with firewalls protecting the perimeter of the company infrastructure doesn’t cut it anymore. To have the highest possible security we need to protect everything inside the perimeter as well.
With the rise of work from anywhere, much due to the pandemic, other problems came to the surface. Social engineering and BYOD is nothing new but when everyone suddenly started working from home to keep the businesses running was on a scale we have never seen before. But how do you tackle the challenges that this new way of working exposed?
This is where Zero Trust Network Access (ZTNA) comes in. It all boils down to that you can never trust any device or any user until you have verified their identity and permissions, even inside the network. Basically deny, never trust, and always verify. It is first after those steps have been taken that you can give access to the resources.
This sounds easy enough in theory, but what does it really mean? Well, any user or device that is trying to connect to the company’s resources will be denied this access as a default. We don’t trust anyone, right? Then we verify the identity of the user or device and also verify the permissions given. It is first after this process has taken place that access is given or kept being denied. In that way, the resources are being kept safe from for example prying eyes or from malware. ZTNA also helps limit damage if anyone or anything should get access to a part of the network through hacking as every part of the network will be isolated through the same deny, never trust, and verify mindset.
Five tips for implementing ZTNA in the organisation
#1: Remember, zero trust is a concept and ZTNA is a way to implement it
The concept of zero trust brings a change in the way we have traditionally approached cyber security. It replaces the implicit trust that is rife in our current networks and that attackers exploit with identity-based trust, which is contextual for that particular organization and is based on their own risk assessment. It is extremely powerful but it needs proper homework on paper before implementing any new tools and technology.
#2: Applications audit – what are your top business/operational applications?
Rather than going for an all-out ZTNA implementation, we recommend including one application at a time. A detailed audit would be needed to include information on which users need access to which services, which application is hosted where and how can users get to the applications in the most efficient way? Companies need to know what belongs where in multicloud environments. Involve the business owners of mission-critical applications from the very beginning and get them on your side. They would need to understand any impact of ZTNA or microsegmentation on the business logic of their applications.
#3: Which application first? That’s a business decision!
This is where understanding business context and risks matter, different organisations might choose different application to start with as appropriate for their business. It’s important to get a quick win first and useful from a change management standpoint as well.
#4: Assess existing tools, if you have NGFW, it’s a good start….
Next-Generation Firewalls (NGFW) are the building blocks of zero trust as they can readily help to enforce strict access controls and segment the network. NGFW can be configured to allow or block access to certain resources or areas of the network based on the user’s role, job function or the type of device being used. NGFWs are most often integrated with application gateways and Security Information and Event Management (SIEM) systems, which provides a comprehensive view of the network and security posture at any given point of time. NGFWs are increasingly designed to slot into ZTNA networks and play a cooperative role in zero-trust frameworks.
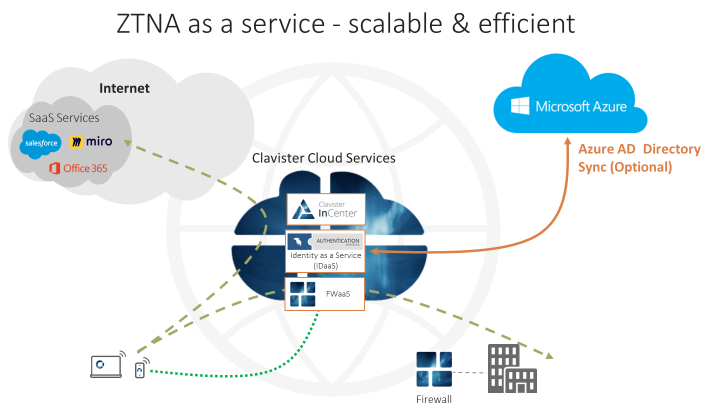
#5: Consider ZTNA as a Service
To be able to cover all applications, whether on-premise or cloud, a scalable and efficient option would be to opt for ZTNA as a service where NGFW and ZTNA client are both in the cloud where verification/authentication mechanisms are applied. This model helps to take away the complexity from the customer’s implementation side and moves the security model towards ‘secure-by-design’.
If you are interested in knowing more, you can watch the recording of Clavister’s webinar on, ‘ZTNA and Clavister’.
For more information on what Clavister can offer in terms of ZTNA, please visit www.clavister.com or contact us today.
Written by:
Neena Sharma, Senior Product Marketing Manager