Reflections on Identity and Automation from Gartner’s Security Summit

The recent Gartner summit in London pointed to one inescapable conclusion: Authentication is the hottest topic in security.
Businesses have spent billions on security solutions—but does any CEO feel safer for all that investment? Data breaches, ransomware situations and corporate hacks reach the headlines with financial impacts reaching into the hundreds of millions USD. I had the privilege to spend last week in London representing Clavister at the Gartner Security & Risk Management Summit. There were visions exchanged and the crowd learned of new research studies on point the way forward for enterprises to take.
The rise of automation
One key concern is the huge shortage of security experts in the industry. Automation becomes a key opportunity to alleviate this problem, making systems that adapt and react to threats without human intervention. However, automation is not simple; introducing and trust becomes key. Gartner has broken it down into the “The Automation Continuum” stretching from “Ad-Hoc Automation”, to “Limited Automation”, via “Functional Automation” to “Integrated Automation” and finally reaching “Adaptive Automation”.
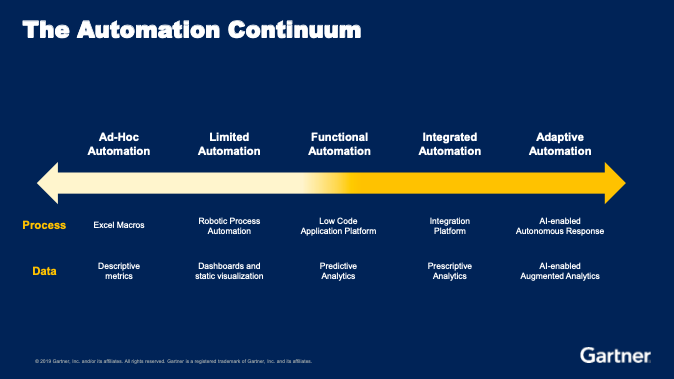
It’s typical of Gartner to model things out like this but I think it’s actually very useful. With automation people typically think of robotics and perhaps fear of losing control—pushing adoption of innovation away. When breaking automation down in steps it’s much easier to plan for quick wins that help the organization and the business in the short term. It helps to see where metrics and dashboards fit in leading to Prescriptive Analytics providing automated key recommendations to actions – before machines take over with full AI-enabled Autonomous Responses. There are a lot a small steps to automate with workflow optimization and there are many quick wins.
Identity is the new parameter
Gartner’s key recommendation to their clients on where to focus first is around the identity. With all perimeter and cloud security solutions in place it’s all for naught if good Identity Management Automation isn’t part of the solution. Criminals don’t have to hack-in, they can just log-in.
Passwords are still the weakest link and it’s a shame that not all businesses have done something about that. 64% of records stolen in 2018 are identities* and 29% of breaches involved the use of stolen credentials**. Yet, only 19% of CISOs think they encountered a stolen credential incident in 2018***. Gartner insists that Multi-factor Authentication (MFA) but also First-time Account Generation (FAG) and Enterprise Password Management (EPM) solutions are first priority to adopt. We couldn’t agree more—Identity is everything—it’s effectively the new perimeter. Complex password policies work against you, multi-factor authentication with mobile push authentication is the solution. This is “Functional Automation” in the security space and it’s should be the highest priority for business of any size to implement.
Gartner’s recommendations on Identity don’t stop there. Privileges are far too powerful and typically not carefully managed. Identity and Access Management or rather Identity Governance solutions need to be implemented with Adaptive Access Approaches so that the right people can reach the right data only from the right place at the right time—when appropriate and approved. It requires a little shift in mindset when even administrators should have a selective access to systems, segments and data. A point made relevant by shipping conglomerate Maersk—who shared their well-reported story of having experience a worldwide meltdown of their IT systems in 2017. The virus that hit them could make so much impact quickly because an administrator’s ‘simple’ password was intercepted by the virus in the days prior to the outbreak. It took them 14 days to get business capabilities back. It took another four weeks until full scale was reached. More selective privileges to admin accounts and MFA would have reduced impact significantly.
This is not only relevant to humans’ interfaces. Much of our business communications and interactions is happening machine-2-machine through application programming interfaces (APIs)—often with simple passwords or one-time keys setup. API security is a big concern. When data is flowing freely between corporations and business models are dependent on it it’s critical to start securing these data exchanges more intimately. At Clavister we know this from the telecom world—where signaling and user-data traffic on roaming links between trusted mobile operators still must be inspected and screened to make sure threats stay out of the home network. The same will be true in the enterprise space. You may trust your partner’s actions but when they’re breached, you’ll still be vulnerable.
Rip off the band aid and do it right
Security has, for too long, been a mere patch on existing business processes. It’s been seen as cumbersome and often seen as only a cost. Now that new business models are invented and adopted there is no better time than to see a fundamental shift. Security needs to be seen and embraced as a benefit—not a burden—and it must be built in from the start enabling the new business paradigm. This is how we can make a differentiated value proposition to our customers and make sure they can enjoy our business model innovations.
Related products:
Clavister EasyAccess
Clavister OneTouch
Terminology:
IAM Identity and Access Management
MFA Multi-factor Authentication
FAG First-time Account Generation
EPM Enterprise Password Management
API Application Programming Interfaces
Sources:
* Breach Level Index – (link)
** “2019 Data Breach Investigations Report,” Verizon (link)
*** “Anticipating the Unknowns: Chief Information Security Officer (CISO) Benchmark Study,” Cisco (link)








