FBI Warns of Multi Factor Authentication SMSs Being Vulnerable
Instead, they advise Biometrics as the new base line for authentication.
Multi-Factor-Authentication (MFA) has been under attack recently by prominent government instances. The American FBI issued a firm warning to enterprises that MFA with OTP SMS is not as safe as it appears to be with wide press coverage in media such as forbes.com and others.
While any MFA might be better than simple passwords, their point is that as telecom signaling networks and processes are inherently NOT safe, using them as methods to process to send passwords is also vulnerable. Granted—it’s not easy to hack an SS7 Network—but if you do, the SMS messages carried over them are readable in clear text. Also, it’s entirely up to the processes of the telecom operator to prevent issuing replacement SIM cards that can potentially clone the phone number to a hacker, directing the OTP SMS to a 3rd party. These methods are fully possible and while they might require some social engineering—for a targeted intercept—hackers will do it.
There’s an additional flaw in the use of One Time Passwords overall—they neglect to ask the question who is using the password. There is no validation that the intended person is actually who he/she says he/she is—therefore not securing data access regulations for many security administrators.
The solution—in the FBI’s and in our eyes—is to use biometric validation of the users when accessing data and services. This is done using a device that many users have in their pockets today—the smartphone. Modern units provide incredible capabilities to validate the user’s identity using fingerprint authentication or facial recognition—regardless if you are an iOS or Android fan. The process is straight forward—you login to your service anywhere using a user-id—which triggers a request to the users’ registered phone via the Over-The-Top notification services (optionally) or simply requires the user to open a specific app on their phone, the user confirms the login with their finger or face—and it’s done. Simple as that, more secure than ever (for sure more than MFA with OTP via SMS anyway!)
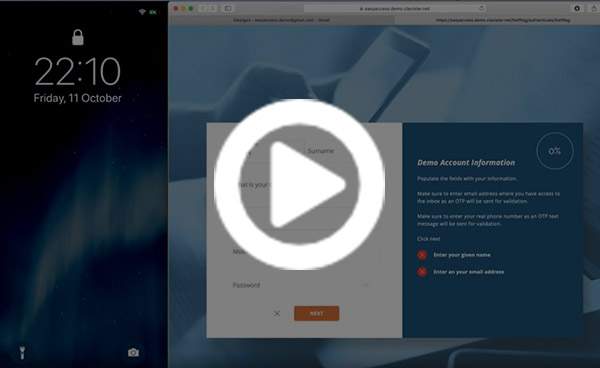
See how this works here:
Clavister provides this type of authentication out of the box with EasyAccess—a Identify and Access Management solution where biometric authentication is the new default for users to gain access. The solution handles both simplified and more secure authentication but also adds single-sign-on to a wide range of services via personalized web portals. This secures that not only is the access secure—also is it more fun to use, saving time for the user with every login.
Try it yourself by creating a demo account here: www.clavister.com/easyaccess/demo
Check out this video to learn how!
Related products:
Clavister EasyAccess
Clavister OneTouch
Terminology:
MFA Multi Factory Authentication
OTP One Time Password
SMS Short Message Service
SS7 Signaling System No 7—a telco ‘language’ to let exchanges talk with each-other, setup calls and exchange messages.
Source:
***https://techworld.idg.se/2.2524/1.724941/fbi-biometrisk-inloggning