The Future of Network Security Is in the Cloud – Introducing Elastic Secure SD-WAN

Security needs are evolving quickly. Twenty years ago, it was enough with a firewall at your network door—ten years ago you sufficed with segmentation—today this is not enough. Users are connecting to your data from everywhere as your business support systems have evolved from a server-room only approach to a hybrid mix of cloud services, hosted systems and on premises IT solutions. Here are the top 3 trends in the security industry and how they impact us:
#1 trend is that passwords are the weakest link… This is not a trend really, it’s a fact and it’s easy to do something about it with Multi-Factor-Authentication (MFA). The trend is that businesses are increasingly focused on implementing MFA and and easing the customer experience to utilize new, easy deployment strategies in the cloud. The benefit is that security administrators finally get certainty of who is accessing what data—and can implement policies based on that.
#2 trend is the ever-increasing level of encrypted traffic – nearly 90% of all web traffic is HTTPS nowadays, leaving firewalls and other equipment transporting those packets in the dark. Threats are encrypted too— and they will sneak right in if traffic is not inspected. The problem is that much more processing capacity is required to decrypt and scan the traffic—in order to protect the enterprises and users. Typical firewalls on the market reduce their capacity by 60-90%* by having inspection built into the box and many don’t include modern scanning methodologies. Capacity on demand is needed in the places where traffic is flowing and growing.
#3 trend is cost reduction – security infrastructure’s cost footprint has to stay manageable while at the same time stay agile to grow with demand. Proprietary transport technology like leased lines and MPLS services are being replaced with SD-WAN technology. Also, the CPEs delivering this is under the loop being transformed to a universal access device even running ARM technology replacing x86 to keep power consumption and cost down.
These trends are a contradictory in their nature, more intelligence and processing needed while at the same time reducing the CPE footprint. The solution is in security-as-a-service capabilities added to CPEs delivered in the cloud as a complement.
Transforming to an Elastic Secure SD-WAN
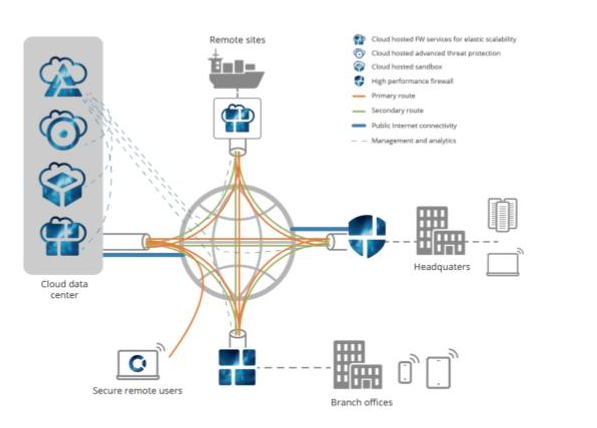
The solution to a new generation security architecture is already here today. Administrators have an opportunity to split up their security use-cases – traditionally delivered in an all in one NGFW package – and place out the workload to different parts of the network. Some use-cases require local placement in the customer premises equipment – but many others perform much better in flexible cloud datacenter infrastructures. At the same time telecom networks are transforming to a Multi-access Edge Commuting (MEC) system – a technology that brings cloud architectures very close to the endpoint in for instance local exchanges, street corner clouds or 5G base-stations. As this infrastructure is rolled out and made accessible on demand – some use-cases can even be run in edge cloud systems.
Gartner calls this new architecture Secure Access Service Edge (SASE, pronounced “sassy”) and really is a solution that scales to the users’ need—at the right time. It may include Secure Web Gateways, Cloud Access Security Brokers and Sandboxing in a centralized datacenter cloud location. Essential services can be run on premises on the CPE still, services such as routing, access lists, segmentation and identification of applications in traffic allowing selective routing. But a majority of the use cases can be run elsewhere, scaling on demand. We call this the Elastic Secure SD-WAN. A SD-WAN that is secure at its core because it’s built on a Firewall—not a router—and has security inherited. Elastic because the solution grows depending both on traffic volume and user scale, but also after use cases are enabled. Virus scanning, Content Filtering, Traffic decryption, API layer scanning etc.
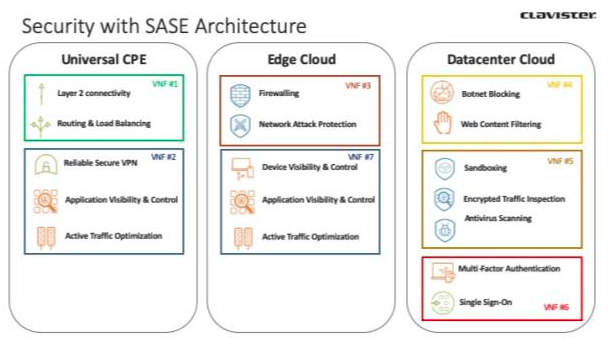
For small branches or sites this trend is particularly important. In particular with many IoT devices involved. The solution is often that security must be embedded in the device or be served on a low-cost CPE running multiple use-cases. ARM CPUs provide a piece of the puzzle here—typically at half the cost of Intel CPU’s they also consume less power and provide powerful computing power for specific use cases. Universal CPE’s (uCPEs) provide another piece of the puzzle—providing the capability to run multiple VMs in the same edge node, allowing for multipurpose devices with the ability to swap out specific components just by installing new software.
Firewalls need to evolve to work in this new environment. They need to be split up use cases in order to work extra efficiently at the edge in the uCPE — taking up as little resources as possible – and support both Intel and ARM processor architectures. They need to be complemented with cloud run services that supply essential add-on security services that are not needed to be run close to the customers and users. Welcome to a new world build with Elastic Secure SD-WAN.
Read more about Elastic Secure SD-WAN in this whitepaper:
https://www.clavister.com/elastic-sd-wan/
Related products:
Clavister NetEye Cloud
Clavister EasyAccess
Clavister NetWall
Clavister OneConnect
Terminology:
SD-WAN – Software Defined Wide Area Networking
SWG – Secure Web Gateway
CASB – Cloud Access Security Broker
SASE – Secure Access Service Edge (pronounced “sassy”)
CPE – Customer Premises Equipment – proprietary equipment’s placed at the customer site
uCPE – Universal Customer Premises Equipment – equipment placed at the customer open to run VNFs with other software functions.
Source:
* https://www.securityweek.com/firewalls-challenged-when-dealing-ssl-traffic-nss-labs








